First Windows 10 exploit
Dark Readings article on our Blackhat presentation. Read here.
With this presentation, we take a new approach to reverse engineering. Instead of attempting to decompile code, we seek to undo the work of the linker and produce relocatable files, the typical output of a compiler. The main benefit of the later technique over the former being that it does work. Once achieved universal code ‘reuse’ by relinking those relocatable objects as arbitrary shared libraries, we'll create a form of binary reflection, add scripting capabilities and in memory debugging using a JIT compiler, to attain automated API prototyping and annotation, which, we will argue, constitutes a primary form of binary code self-awareness. Finally, we'll see how abusing the dynamic linker internals shall elegantly solve a number of complex tasks for us, such as calling a given function within a binary without having to craft a valid input to reach it. The applications in terms of vulnerability exploitation, functional testing, static analysis validation and more generally computer wizardry being tremendous, we'll have fun demoing some new exploits in real life applications, and commit public program profanity, such as turning PEs into ELFs, functional scripting of sshd in memory, stealing crypto routines without even disassembling them, among other things that were never supposed to work. All the above techniques have been implemented into the Wichcraft Compiler Collection, released as open source software (MIT/BSD-2 licenses).
In this presentation, we detail a new attack vector against SMBv2, affecting all versions of IE, including the Spartan version shipped with Windows10. While attacks involving SMB have long time been common in LANs, our attack allows complete user compromise from the internet. By leveraging a series of bugs and malfunctions, we'll see how remote credentials theft or user impersonation can be performed without user interaction, extremely reliably, and from the Internet.


The original whitepaper is archived on the Blackhat website. The latest version is available on slideshare.
Xml eXternal Entities (XXE) is one of the deadliest vulnerabilities on the Internet, and we will demonstrate how critical enterprise software packages are still vulnerable to these attacks today. In this action-packed presentation, we will demonstrate two 0-day vulnerabilities we identified in both popular server (Java) and client-side (Internet Explorer) technologies. The first vulnerability can be exploited with an attacker-controlled XML leading to arbitrary file ex-filtration on a target server even with all the Java protections enabled. The second vulnerability allows an attacker to steal both arbitrary files on the local hard drive and secret information across origins with a malicious webpage. Therefore, effectively bypassing the Same Origin Policy and breaching the web-local separation. Both exploits are reliable and do not depend on memory corruptions.


The Microsoft security bulletin for MS15-039 (Important) is available on the Microsoft website.

The original whitepaper is archived on the Blackhat website. The latest version is available on slideshare.
Xml eXternal Entities (XXE) is one of the deadliest vulnerabilities on the Internet, and we will demonstrate how critical enterprise software packages are still vulnerable to these attacks today. In this action-packed presentation, we will demonstrate two 0-day vulnerabilities we identified in both popular server (Java) and client-side (Internet Explorer) technologies. The first vulnerability can be exploited with an attacker-controlled XML leading to arbitrary file ex-filtration on a target server even with all the Java protections enabled. The second vulnerability allows an attacker to steal both arbitrary files on the local hard drive and secret information across origins with a malicious webpage. Therefore, effectively bypassing the Same Origin Policy and breaching the web-local separation. Both exploits are reliable and do not depend on memory corruptions.


The original whitepaper is archived on the Blackhat website. The latest version is available on slideshare.
This presentation will demonstrate that permanent backdooring of hardware is practical. We have built a generic proof of concept malware for the intel architecture, Rakshasa, capable of infecting more than a hundred of different motherboards. The first net effect of Rakshasa is to disable NX permanently and remove SMM related fixes from the BIOS, resulting in permanent lowering of the security of the backdoored computer, even after complete erasing of hard disks and reinstallations of a new operating system. We shall also demonstrate that pre-existing work on MBR subversions such as bootkiting and preboot authentication software brute force can be embedded in Rakshasa with little effort. More over, Rakshasa is built on top of free software, including the Coreboot project, meaning that most of its source code is already public. This presentation will take a deep dive into Coreboot and hardware components such as the BIOS, CMOS and PIC embedded on the motherboard, before detailing the inner workings of Rakshasa and demo its capabilities. It is hoped to raise awareness of the security community regarding the dangers associated with non open source firmware shipped with any computer and question their integrity. This shall also result in upgrading the best practices for forensics and post intrusion analysis by including the afore mentioned firmware as part of their scope of work.

Wikipedia describes Rakshasa as the first public demonstration of a permanent firmware backdoor.

The original slides are archived on the DEF CON website. The latest version is available on slideshare (190 000+ views).

Rakshasa has been featured in the MIT Technology review as a backdoor "Undetectable and Uncurable".

Forbes published an article outlining the disruptive innovations behind Rakshasa.
Attend Rakshasa's presentation with this video from Blackhat USA 2012.
In this presentation, we introduce a new exploitation methodology of invalid memory reads and writes, based on dataflow analysis after a memory corruption bug has occurred inside a running process.
We will expose a methodology which shall help writting a reliable exploit out of a PoC triggering an invalid memory write, in presence of security defense mechanisme such as compiler enhancements (full RELRO, SSP...), or kernel anti exploitation features (ASLR, NX...).
We will demonstrate how to find all the function pointers inside a running process, how to determine which ones would have been de-referenced after the crash, which ones are truncable (in particular with 0x00000000). In case all of the above fail, how to test for specific locations overwrites in order to indirectly trigger a second vulnerability allowing greater control and eventually control flow hijacking. All of the above without source code, indeed.
In the case of invalid memory reads, we will exemplify how indirectly influence the control flow of execution by reading arbitrary values, how to trace all the unaligned memory access and how to test if an invalid read can be turned into an invalid write or used to infer the mapping of the binary.
We will also introduce a new debugging technique which allows for very effective testing of all of the above by forcing the debugged process to fork(). Automatically. And with a rating of the best read/write location based on probabilities of mapping addresses (because of ASLR).
Finally, since overwriting function pointers doesn't allow direct shellcode execution because of W^X mappings, we introduce a new exploitation technique which works even in the most hardcore kernels such as grsecurity. IT is called "stack desynchronization" and allows frame faking inside the stack itself.
Those techniques are implemented in the form of a proof of concept tool running under x86 GNU/Linux available as open source : here.


The PMCMA debugger is free software (Apache License) and is available on github.

The original whitepaper is archived on the Blackhat website. The latest version is available on slideshare.
In the last 5 years, virtualization software has been massively adopted by companies as a mean to reduce costs, achieve instant scalability, and possibly better their security through isolation. Recent numbers indicate that 78 percent of companies have their production servers virtualized, and 20 percent of them actually only rely on virtualized servers. At the same time, security auditing of such software poses unique challenges, in particular when it comes to dynamic testing. In this paper, we describe a methodology for the security assessment of virtualization software based on switching the CPU mode to virtual 8086 mode in order to get access to the (possibly virtualized) hardware, that aims at being both generic (applicable to both x86 and x64 architectures) and extremely large in terms of code coverage. We have implemented this technology under the form of a dynamic testing tool which has proved to be very efficient in finding bugs in virtualization software.


Download the Slides of this presentation from the archives of HITB Asmterdam website.

Download the Slides of this presentation from the archives of Ruxcon website.

Download the Slides of this presentation from the archives of HITB Kuala Lumpur website.
Pre-boot authentication software, in particular full hard disk encryption software, play a key role in preventing information theft. In this paper, we present a new class of vulnerabilities affecting multiple high value pre-boot authentication software, including the latest Microsoft disk encryption technology : Microsoft Vista's Bitlocker, with TPM chip enabled. Because Pre-boot authentication software programmers commonly make wrong assumptions about the inner workings of the BIOS interruptions responsible for handling keyboard input, they typically use the BIOS API without flushing or initializing the BIOS internal keyboard buffer. Therefore, any user input including plain text passwords remains in memory at a given physical location. In this article, we first present a detailed analysis of this new class of vulnerabilities and generic exploits for Windows and Unix platforms under x86 architectures. Unlike current academic researches aiming at extracting information from the RAM, our practical methodology does not require any physical access to the computer to extract plain text passwords from the physical memory. In a second part, we will present how this information leakage combined with usage of the BIOS API without careful initialization of the BIOS keyboard buffer can lead to computer reboot without console access and full security bypass of the pre-boot authentication pin if an attacker has enough privileges to modify the bootloader. Other related work includes information leakage from CPU caches, reading physical memory thanks to firewire and switching CPU modes.

The audio recordings of the presentation are available from the DEF CON archives.
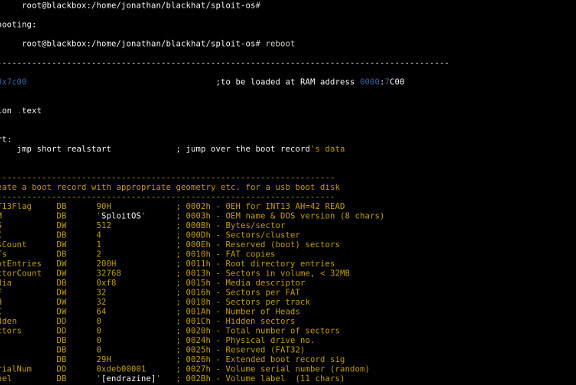
All of the exploits presented during the conference are available from a single zip archive (Kernel exploits, user land assembly exploits, SploitOS.asm).
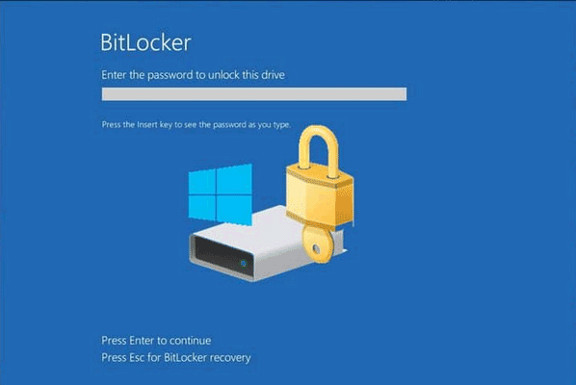
The advisory for vulnerability CVE-2008-3893 affecting Microsoft Bitlocker is available here.

The advisory for vulnerability CVE-2008-3899 affecting TrueCrypt is available here.

DEFCON 16 - BIOS: Bypassing Preboot Authentication Passwords

Blackhat 2015 SMB Sharing More than your files

Blackhat 2015 SMBv2 Sharing More Than Just Your Files

Ruxmon 2012 Reverse Engineering Proprietary Protocols

Blackhat 2015 XXE Defenseless JDK XML Parsers JAVA

Blackhat Europe 2016 Witchcraft Compiler Collection-Towards Self Aware Computer Programs-wp

Blackhat USA 2011 Post Memory Corruption Memory Analysis PMCMA

Blackhat USA 2012 Hardware Backdooring is Practical

Blackhat 2011 Post Memory Corruption Memory Analysis Whitepaper

DEFCON 24 Introduction-to-the-Witchcraft-Compiler-Collection

BSides San Francisco 2016 Witchcraft Compiler Collection

HackitoErgoSum 2010 Breaking Virtualization 8088 mode

Blackhat 2016 Witchcraft-Compiler-Collection User Manual
Index of miscellaneous low level tools (BIOS, debuggers, kernel code, exploits).
Latest codebase of the Witchcraft Compiler Collection.
Latest codebase of the Post Memory Corruption Memory Analyzer (PMCMA).
Local copy of the Witchcraft Compiler Collection.